Recognizing the cybersecurity dangers posed by modern chip designs and accessible devices, the Defense Advanced Research Projects Agency (DARPA) has created a new program dedicated to spreading scalable chip security through automation.
The Automatic Implementation of Secure Silicon (AISS) program will focus on overcoming the economic and technical challenges involved in such incorporation. These problems include the sheer expense of the matter, as well as the time investment, level of expertise required, as well as the issues of balancing size, performance and power dissipation figures with what these systems need to function.
“Today, it can take six to nine months to design a modern chip, and twice as long if you want to make that same design secure,” Serge Leef, a program manager in DARPA’s Microsystems Technology Office (MTO), said. “While large merchant semiconductor companies are investing in in-house personnel to manually incorporate security into their high-volume silicon, mid-size chip companies, system houses, and start-ups with small design teams who create lower volume chips lack the resources and economic drivers to support the necessary investment in scalable security mechanisms, leaving a majority of today’s chips largely unprotected.”
Once designed and launched, experts noted that adding further security to chips is nearly impossible. AISS, therefore, wants a new, automated chip design flow that will give security systems the ability to scale their efforts to those designs. Designers would still have room to work, too, letting them find their own balances in economics, security and design productivity.
“Strategies for resisting threats vary widely in cost, complexity, and invasiveness. As such, AISS will help designers assess which defense mechanisms are most appropriate based on the potential attack surface and the likelihood of a compromise,” Leef said.
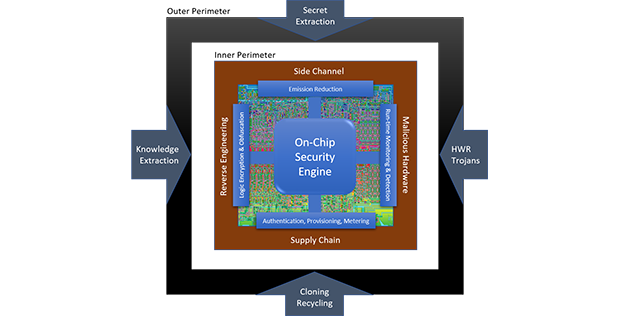
The proposed system will include two partitions, consisting of an application specific processor partition and a security partition that installs on-chip security features. Using such methods, AISS hopes to respond to side channel attacks, reverse engineering attacks, supply chain attacks and malicious hardware attacks.




